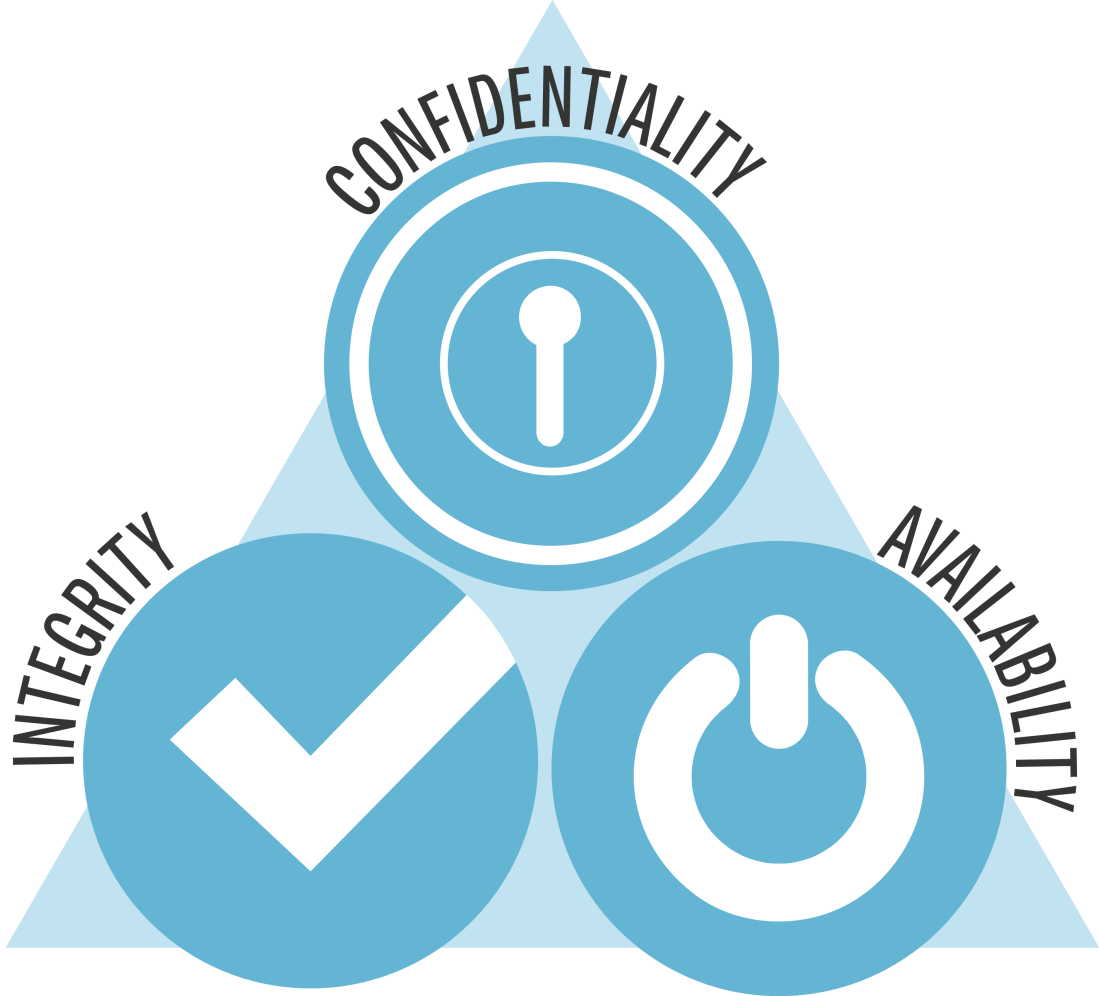
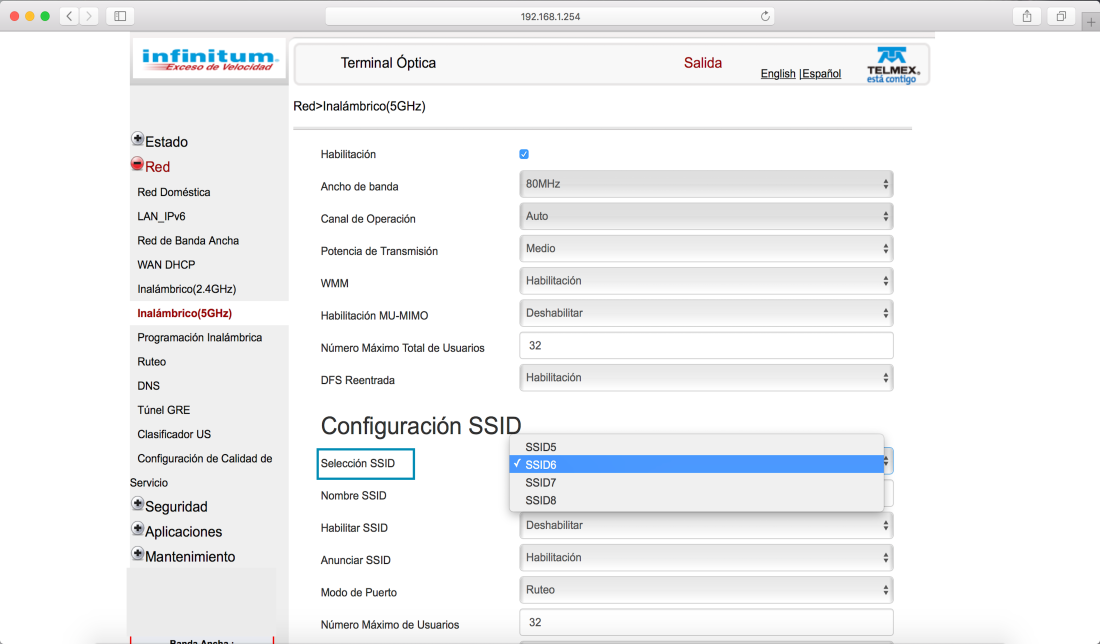
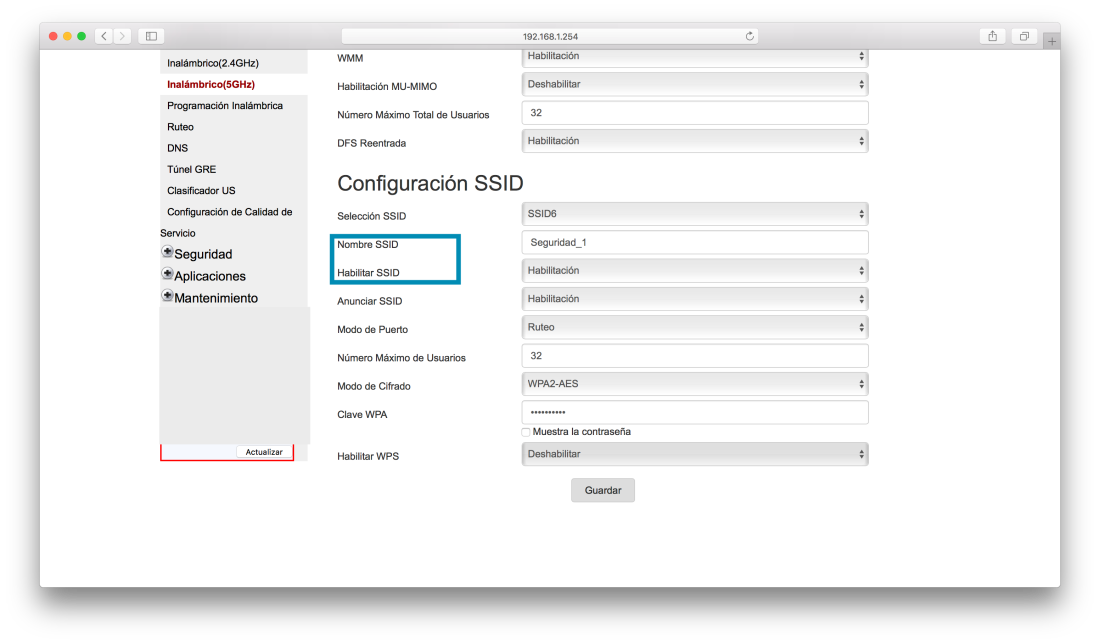
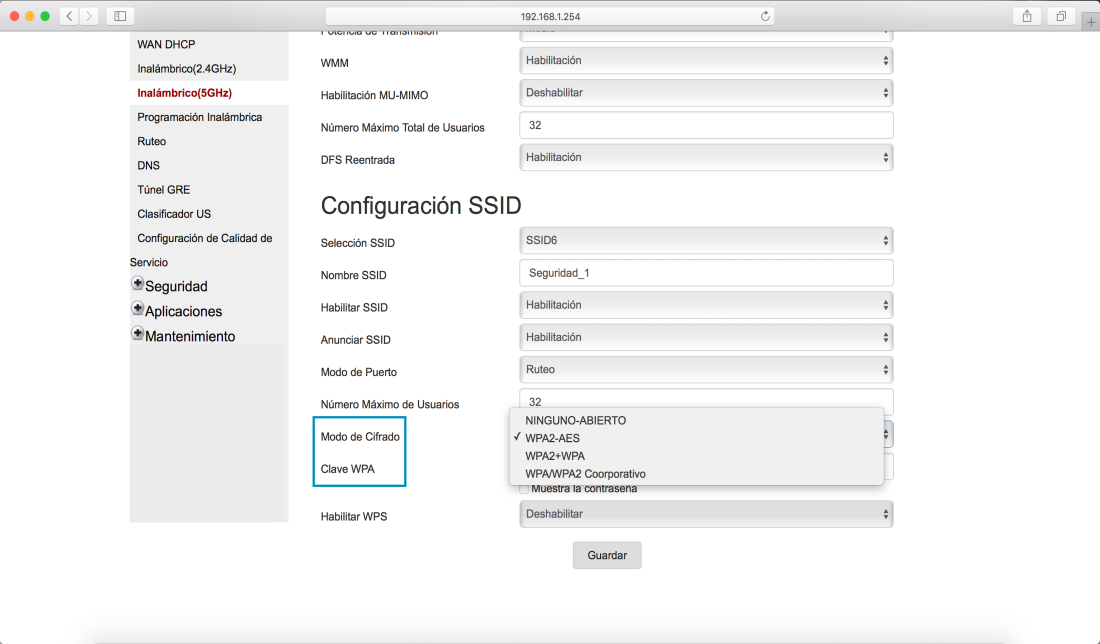
Each day, we log into many different webpages, they ask for authentication. We need to prove that we are us, but why is it so important? Also, how does it works? Authentication is needed to access to personal information, social media, at work, unlocking the phone, anywhere. It is almost a requisite to join every webpage to access to certain content. Regarding security, it is the way to block your information for the resto of the world. There are many different ways to prove that you are really you. Commonly, sites ask for a password, but they aren’t the only option. The next video uses interesting examples to explain the importance of authentication.
- Knowledge factors: sometimes, the service that is asking for authentication can ask for names, specific questions, PIN numbers, or the password itself. Those are known as knowledge factors.
- Possession factors: these are the ones that the user has in possession, such as ID cards, one-time password tokens, specific codes, or any artifact that can prove your authentication.
- Inherence factors: this authentication factor covers the biometrics of the user, such as fingerprint scans, facial recognition, voice recognition, retina scans, iris scans, between others.

A modern way to authenticate the user is its location depending on the cellphone. This also has to do within its device activity and many other complex factors. Nowadays, it is recommended to use at least two factor authentications at the time per each account. For example, it is possible to activate an account with password and with a pin provided by the service company via cellphone.
There are may authentication tools in the market. It is important to be secure and also to protect your personal information. It can be annoying to unlock the accounts with more than 1-factor-authentication, but sometimes it is necessary to improve the security of our accounts. Remember, it’s our personal information that is being protected.
References
What is user authentication? – Definition from WhatIs.com. (2018). Retrieved from https://searchsecurity.techtarget.com/definition/user-authentication